Data privacy and protection of personal information – it’s something we know matters, but we don’t really talk about. Until now that is. With increasing legislation and tighter regulations, enterprises are facing more mandates to protect personal and sensitive information. As a result, the cost for non-compliance can be high.
The changing digital landscape
COVID-19 accelerated our move online, and whether for shopping, entertainment or critical services like banking, many of us share everything from name and address to credit card details over the Internet. In this expanding digital world, securing the wealth of data collected by businesses, health and finance organizations, charities or government bodies is becoming ever-more pressing.
Thinking about your own organization – how well are you really doing in your quest to protect your customers’ personal information? What steps should you be taking to secure this data against increasingly determined bad actors?
Whose responsibility is it anyway?
How responsible an organization comes down to whether they have assigned accountability and responsibility for protecting information – and who to. As we move from an era of information on paper to information collected, processed and stored in computer systems, accountability and responsibility seems to have shifted from the process/information owner to the system owner, or the CIO.
With that in mind, should organizations be outsourcing accountability when they outsource business processes or system management to a third-party?
Ask yourself, if you know:
- The type and value of information collected
- Where that personal or sensitive information is
- Who has access to that information
- Who is protecting it
- How well it is protected
Let’s start from the top
Enterprises who suffer leaks or data breaches face potential penalization by authorities, lawsuits from clients whose personal information have been released – plus loss of critical trust in their organization. All negatively impacting their branding and image. In some jurisdictions like Australia, Canada, the UK and US, corporate directors can be held personally liable for failing to manage cyber risk and reasonably protect data and information. And yet, cyber security concerns are still underrepresented at a board and executive leadership team (ELT) level.
The key is to ensure reasonable measures – both mandatory and discretionary – are implemented to protect data and information throughout its lifecycle. Reasonable measures could depend on factors such as an organization’s risk appetite and tolerance levels, internal/external influences in terms of mission and objectives, stakeholder requirements, legal and regulatory requirements, or contractual obligations.
However they are determined, these measures should flow through the organization from the ELT to operational levels – as shown here. The FDIC’s Enterprise Architecture Framework, NIST’s Enterprise Architecture Model or even an information security standard – such as ISO27001 Information Security Standard or NIST’s Cyber Security Framework – are all good places to start.
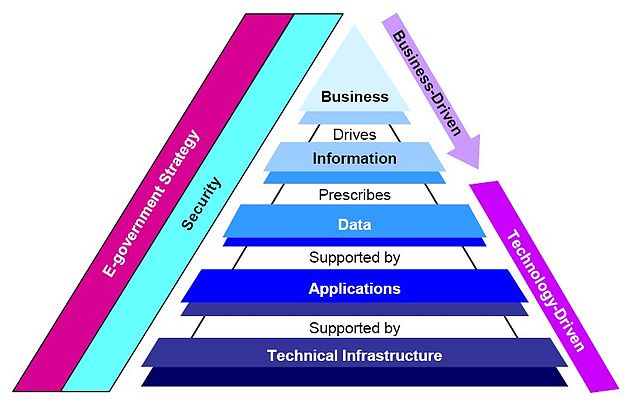
FDIC’s Enterprise Architecture Framework[1]
Increased threat calls for robust governance
With security threats like ransomware during the COVID-19 pandemic becoming more prevalent, the risk to organizations from information loss and the resulting damage is greater than ever.
To control this risk, it makes sense to establish a governance structure that promotes accountability and responsibility towards the protection of information. This can bring about a paradigm shift in leadership commitment to information security.
As the second part of the strategy, an information security risk management framework can facilitate the management of threats and risk from collecting, processing and storing business critical or personal and sensitive information. Aligning this framework to the enterprise risk management framework will help ensure that protecting information goes hand-in-hand with meeting business objectives.
Once these frameworks are in place, the collection, processing and storing of information can be risk-assessed. This assessment can be used to determine what needs protecting, how it should be protected, and who should be responsible. Then appropriate operational measures can be put in place, including:
Information identification, classification, and labelling
This includes establishing guidelines for technical solutions and administrative controls (processes and operational documentation) that should be used through the information lifecycle, from receipt to storage or destruction. Consider:
- How long you store information (whether for us in analytics or investigating an incident, or as required by law or court order)
- The acceptable ways to store or destroy information
- How you can control leaks while information is being used
- Which controls can help ensure only the authorized people are able to access information stored in your systems
Technical controls to protect critical and sensitive information, including:
- Identity management (multi-factor authentication, single sign on verification and authentication)
- Access to your network environment (unified threat management solutions, network segregation to protect critical and sensitive data from non-critical and sensitive data)
- Supporting incident identification and response (reporting tool)
Audit log and monitoring
This entails the proactive monitoring of activities logged. Proactive monitoring enables you to be alert to potential threats and take action as soon as a possible threat is recognized – instead of acting only once information has been leaked or breached. This requires a balance of technical solutions and threat intelligence which small- and medium-size organizations may prefer to outsource to third-party managed security service providers.
Security threat detection, response and reporting
This includes the possibility of establishing a security incident response team, communication cascade, and retainer service for digital forensics and incident response.
A considered approach can combat risk
In the face of limited resources and capabilities, a responsible approach to data protection requires governance and direction over which security measures should and can be implemented. Prioritizing the implementation of these security measures through a risk-based approach is key, in addition to using an information security management system (ISMS) framework managed by the Board and ELT.
Find out how the team at Lumen can support your organization in establishing your governance framework.
LUMEN CONNECTED SECURITY
Automated threat detection. Built in protection.
See more, Stop more.
Equip your organization with the right security services