The threat from ransomware – and the money cybercriminals are making – has never been greater. Cyberattacks on organizations of all kinds across the world are prolific, up 102% from 2020, with organizations in Asia Pacific seeing the highest number of ransomware attacks – 51 per week, according to Check Point Research. The average ransom demand climbed more than 500% between 2020 and 2021, with the average payout spiking 82% in that period.[1]
“
The average ransom demand climbed more than 500% between 2020 and 2021, with the average payout spiking 82% in that period.
Cybercriminals are using increasingly sophisticated tactics like “Double Encryption Attacks” to strengthen the likelihood of ransom payments. In these type of attacks, cybercriminals scan the target organization’s network to identify & exfiltrate sensitive data before encrypting the setup, or in some instances, they also locate and destroy backup files before launching the attack itself. Thus, the organization often has limited options but to pay the ransom since restoration from functional backups has been compromised Furthermore, the hackers also commonly threaten to release sensitive corporate data to the public or Dark Net, even if the organization manages to adequately restore their IT systems.
For example, in 2021 a major global oil and gas company was recently forced to shut down their operations and pay a multi-million dollar ransom in cryptocurrency to hackers who stole nearly hundreds of gigabytes of data and threatened to release it publicly.
With nearly 40% of ransomware families discovered in 2020 demonstrating data exfiltration capabilities2, it’s clear that no organization is safe from this critical and growing threat.
You Think You’re Protected. But Are You?
For many organizations, despite their investments in IT cybersecurity defenses they are still susceptible to Double Extortion Attacks.
Enterprise IT systems are typically set up to trust, or whitelist, IP addresses and certificates from their preferred suppliers, as this diagram shows:
Source: Lumen & IDC Webinar – Securing the Digital Trust
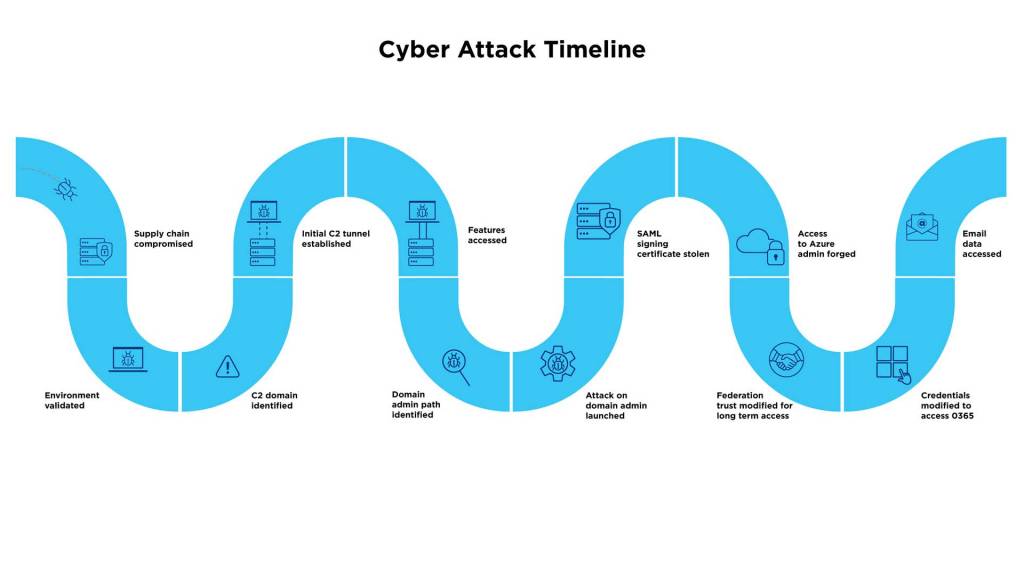
However, this example of a Supply Chain Attack timeline demonstrates how detection-centric tools will only alert your organization to an attack after it has begun – making it virtually impossible to prevent.
Once they’ve infiltrated the system, hackers typically maintain a very light malware footprint, thus allowing them to avoid detection by most traditional cybersecurity systems.
A new emerging trend in attacks is even more sophisticated, and is called a Triple Extortion Attack. In this situation, attackers will steal sensitive data and parse it to find details about their end customers. Once they are able to identify the sensitive data of high net-worth individuals or companies, the bad actors will demand a ransom from these secondary victim as well, with the threat of leaking their data. The primary victims are then vulnerable not only to direct financial losses, regulatory and negative publicity, but also potential lawsuits from secondary victims whose data was compromised.
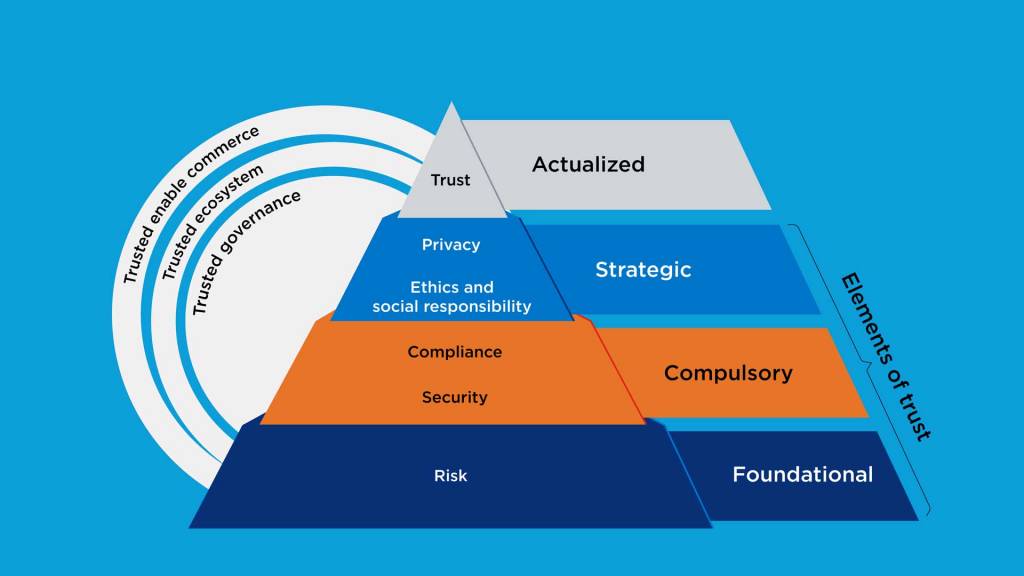
Why a Multi-layered Defense is your Best Weapon
In the case of double and triple extortion attacks, ‘prevention’ is significantly better than ‘cure’. Systems that can detect anomalous user activities, as well as scan and system sweeps, are best suited to proactive protect against ransomware.
At Lumen, we’ve learnt that a successful mitigation strategy requires a multi-pronged approach:
- Advanced multi-factor detection
- Predictive analytics
- Threat vector correlation
- Distinguishing between malicious and normal traffic
How can my Organization Achieve a Multi-defense System Approach?
The first weapon in your armory against double threat attacks is awareness and vigilance; if your users are not trained adequately to spot cyberattacks, your organization’s defenses can easily be breached.
To overcome the threat of ransomware, many organizations deploy Endpoint Detection and Response (EDR) solutions, which can detect and prevent attacks that are propagated through phishing vector. While a EDR solutions’ capabilities are able to stop the encryption stage of an attack and roll back the affected endpoint to a healthy state, they are not able to detect network compromise or bad actors lurking within your network. Neither can EDR prevent data exfiltration before the encryption stage of the attack. Automated solutions such as User and Entity Behavioral Analytics (UEBA) are important complementary additions to EDR investments, as UEBA solutions are designed to spot abnormal activities including network scanning and suspicious data extraction. Leveraging a combination of multi-factor and extended threat detection capabilities which looks at network traffic through log correlation, and identifying suspicious user activities such as data exfiltration through UEBA, will enhance an organization’s security posture and risk mitigation.
Finally, security is not something you can simply set and forget. Good cybersecurity defense practice calls for continuous review and recalibration of your policy controls and processes, to ensure your tools can continue to provide the defense your organization needs.
“
Remember, bad hackers need to be successful only once, whereas you need to be successful all the time.
– Wai Kit Cheah, Director, Security Practice at Lumen Technologies
Your Attack Protection Checklist
How many does your organization have in place?
- Regular vulnerability assessment scans and Risk Prioritization
- A Penetration testing exercise conducted at least annually
- Disciplined Patching
- Limiting user privileges (least privilege principle)
- Continuous Security Log Monitoring
- Remote access only through secured channels
- MFA for all users
- A program of continuous cyber awareness education for employees
If you haven’t checked all these boxes, you’re leaving your organization open to attack.
[2] Attack landscape update: Ransomware 2.0, automated recon, and supply chain attacks
This content is provided for informational purposes only and may require additional research and substantiation by the end user. In addition, the information is provided “as is” without any warranty or condition of any kind, either express or implied. Use of this information is at the end user’s own risk. Lumen does not warrant that the information will meet the end user’s requirements or that the implementation or usage of this information will result in the desired outcome of the end user. This document represents Lumen’s products and offerings as of the date of issue. Services not available everywhere. Business customers only. Lumen may change or cancel products and services or substitute similar products and services at its sole discretion without notice. All third-party company and product or service names referenced in this article are for identification purposes only and do not imply endorsement or affiliation with Lumen. ©2022 Lumen Technologies. All Rights Reserved.
What would you do to prevent a Double-tap attack?
Find out more about cybersecurity defense strategies in light of double and triple threat attacks in our latest video.